Security Overview and Policies
The complete technology stack to be used to support the study includes a mobile app which interfaces with the study participant, and a hosted service managed by Sage which collects the data. This document is concerned primarily with the security of participant data once it has been transmitted to the server. A complete understanding of the security and deidentification risks must also consider the security of user data on the mobile device. However, at this time Sage can not speak to issues related to the security and privacy of participant data that arise from the mobile portion of the technology stack.
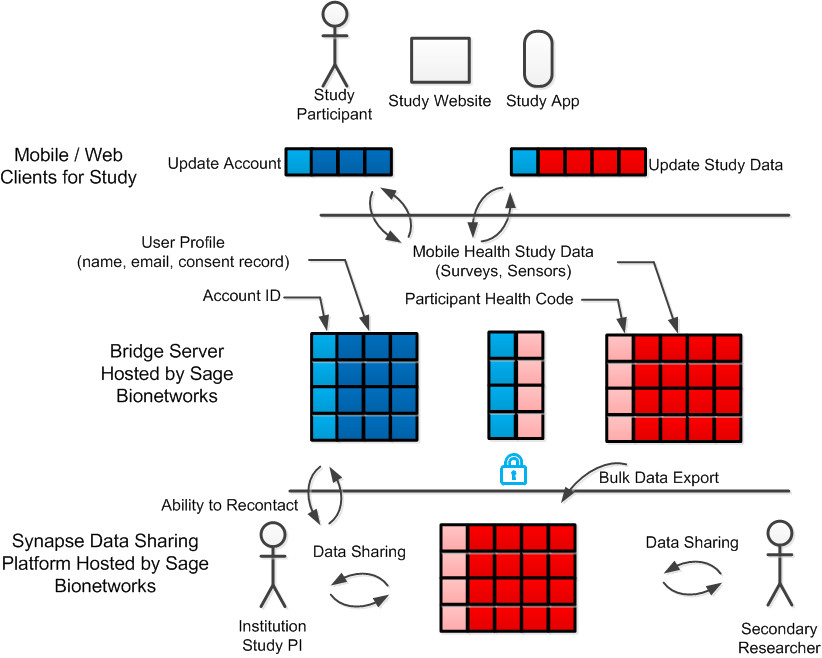
Participants in a study will typically interact with a mobile application designed for that study, plus potentially other interfaces such as a web application. Separate services are provided for updating account and consent information (blue) such as name, emails, or potentially other contact info and for the study-specific and anonymous health data (red). Both types of data are updated when a client application makes a call to the server using the participant’s authenticated account identifier (light blue). A mapping between account ID and a participant health code (pink) is managed automatically by the server allowing study data to be stored and exported without revealing participant identities. This achieves a key goal of the service: the ability to provide coded data sets to researchers outside of the original study team for use in new research projects. Study investigators, but not secondary researchers would additionally have the ability to obtain the participant's account information including consents, but not the mapping between account data and study health code. Sage provides the Synapse Server as the system through which Bridge research data can be distributed to secondary researchers, in a manner consistent with IRB and other governance requirements.
The server portions of this system are implemented using Cloud Providers used by Bridge Server. All communication between components in this system is via standard HTTPS. Management of user account data is achieved as the server consists of a proxy layer on top of Stormpath, a commercial authentication as a service provider. Transfer of Study Data to Bridge describes how coded medical data is received by the system. A secure, encrypted Mapping between Accounts and Study Data is maintained automatically by the server.