Bypass Login Throttling
The Problem
As described in Increase Password Strength (deprecated as of 12/04/2018), we added throttling on logging in (PLFM-3818) to protect our user accounts from being hacked. With this in place, after 10 failed attempts, a user will be locked out for 5 minutes. Now when a hacker attempts to login 10 times on all Synapse accounts every five minutes, all Synapse accounts will be locked.
The Approach
We need a way to identify the real users and do not throttle them. To identify a real users, we may keep some information about the users who had successfully logged in. The next time they try to login, if they provide these information, we let them bypass throttling. This allows our throttling mechanism work against the hacker, but not against our users.
The information we need from the users
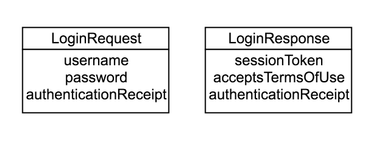
- Username
- Password
- Authentication Receipt that we provide to the user after they successfully login
When a user login, if they give us
- username and password
- we will direct them to the old APIs and they may get throttled
- username, password, and authenticationReceipt
- we will look up to see if we have a record of this receipt for this username
- If so, we let them bypass throttling
- If they successfully login, they will get a new authenticationReceipt
This approach requires all clients to implement the new APIs, cache and provide the cached authenticationReceipt on behalf of the user.
Models
APIs
| Action | Require Authentication | URI | Method | Request Param | Request Body | Response Body |
|---|---|---|---|---|---|---|
| Login | False | /login | POST | LoginRequest | LoginResponse |
See:
PLFM-3824 - Getting issue details... STATUS